Simplifying Access with Single Sign-On (SSO)
Introduction
Single Sign-On (SSO) is a revolutionary technology that allows users to access multiple applications with just one set of credentials. In today’s fast-paced digital world, the importance of SSO for modern businesses cannot be overstated. This blog post will delve into the intricacies of Single Sign-On, exploring its evolution, functionality, benefits, challenges, and best practices.
What is Single Sign-On (SSO)?
Single Sign-On is a method that enables users to log in once and gain access to multiple applications without having to re-enter their credentials. By eliminating the need for multiple logins, SSO simplifies the access management process and enhances user convenience.
Importance of SSO for modern businesses
In an era where efficiency and productivity are paramount, SSO plays a crucial role in streamlining access to various applications. With the increasing complexity of IT environments, SSO provides a seamless and secure way for users to navigate multiple systems with ease.
Evolution of SSO technology
The concept of Single Sign-On has evolved significantly over the years, adapting to the changing needs of businesses and users. From traditional password-based SSO to modern solutions that incorporate biometric authentication and multi-factor authentication, the technology continues to evolve to meet the demands of the digital age.
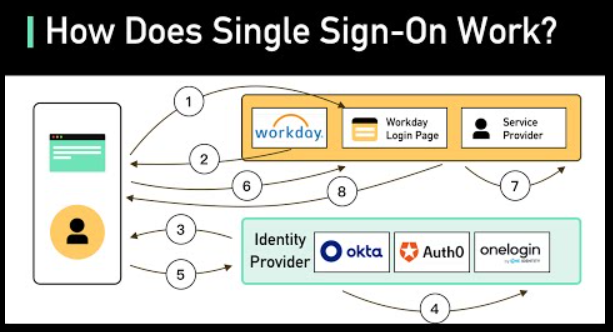
How Single Sign-On Works
Understanding the authentication process
SSO works by authenticating users once they log in to a single system, which then grants access to multiple applications without the need for additional logins. This process not only saves time but also enhances security by reducing the number of passwords users need to remember.
Key components of SSO architecture
The key components of an SSO system include the identity provider, service provider, and user. The identity provider authenticates users, while the service provider grants access to specific applications. The user benefits from a seamless login experience across different platforms.
Different SSO protocols and standards
There are several protocols and standards used in the implementation of SSO, such as SAML, OAuth, and OpenID Connect. Each protocol has its own set of features and capabilities, catering to the diverse needs of organizations and applications.
Benefits of Implementing Single Sign-On
Enhanced user experience and productivity
SSO simplifies the login process for users, enabling them to access applications quickly and efficiently. This seamless user experience boosts productivity and satisfaction, leading to improved overall performance.
Improved security and compliance
By reducing the number of passwords users need to manage, SSO enhances security and minimizes the risk of credential theft. Additionally, SSO helps organizations comply with regulatory requirements by implementing strong authentication measures.
Cost savings and reduced IT burden
Implementing SSO can result in cost savings for organizations by reducing password-related support calls and streamlining access management processes. Moreover, IT teams can focus on more strategic initiatives, rather than spending time on password resets and user access issues.
Challenges and Considerations for Single Sign-On
Integration with legacy systems
One of the major challenges of implementing SSO is integrating it with existing legacy systems that may not support modern authentication protocols. Organizations need to carefully plan the migration process to ensure seamless integration.
User adoption and training
While SSO offers numerous benefits, organizations must ensure proper user adoption and training to maximize its effectiveness. Educating users on the benefits of SSO and providing adequate training can help overcome resistance to change.
Potential security risks and mitigation strategies
Despite its security benefits, SSO can pose risks such as unauthorized access and identity theft. Organizations must implement robust security measures, such as multi-factor authentication and regular security audits, to mitigate these risks effectively.
Best Practices for Successful Single Sign-On Implementation
Establishing clear objectives and requirements
Before implementing SSO, organizations should define clear objectives and requirements to ensure its successful deployment. By setting achievable goals and outlining specific needs, organizations can tailor their SSO solution to meet their unique requirements.
Choosing the right SSO solution for your organization
There are various SSO solutions available, each with its own features and capabilities. Organizations should carefully evaluate different options and choose a solution that aligns with their business requirements, budget constraints, and security considerations.
Testing, monitoring, and continuous improvement
Once SSO is implemented, organizations should conduct thorough testing and monitoring to ensure its effectiveness. Regularly assessing the performance of SSO, gathering user feedback, and making necessary improvements are essential for the long-term success of the system.
Conclusion
In conclusion, Single Sign-On offers a streamlined approach to access management, providing users with convenience, security, and efficiency. By understanding the technology, benefits, challenges, and best practices, organizations can make informed decisions to optimize their SSO implementation.
Remember, implementing Single Sign-On is not just about simplifying access—it’s about enhancing security, improving productivity, and fostering a seamless user experience. With the right approach and a clear understanding of the technology, organizations can unlock the full potential of Single Sign-On.